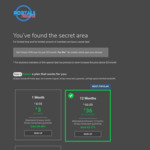
Greetings everyone, next generation decentralized VPN (Portals) is offering special deal to get VPN for 3 USD /month for life:
- No matter which plan you choose, so you don’t have to subscribe for a 3+ years to get this price
- $3/m is valid for renewals as well, for your entire life
How Portals is different:
- instead of connecting to central VPN server, you’re being connected to one of many decentralized nodes (mostly - residential IPs)
- the nodes are being hosted by independent operators (mostly ordinary people sharing their home Internet to you)
- so contrary to centralized VPN, your traffic doesn’t go through company owned servers, but through different AND independent nodes
- this makes Portals better at a) privacy, as Portals cannot monitor your traffic even if they wanted to b) better at passing through Netflix blocking algorithms, which increasingly detect centralized VPN servers
As a fresh concept, it's still under heavy development/improvement, but in case something goes south they tend to extend service or offer some kind of promo/gift.
Supported systems: Android, MacOS.
No, but any of the endpoint operators can.